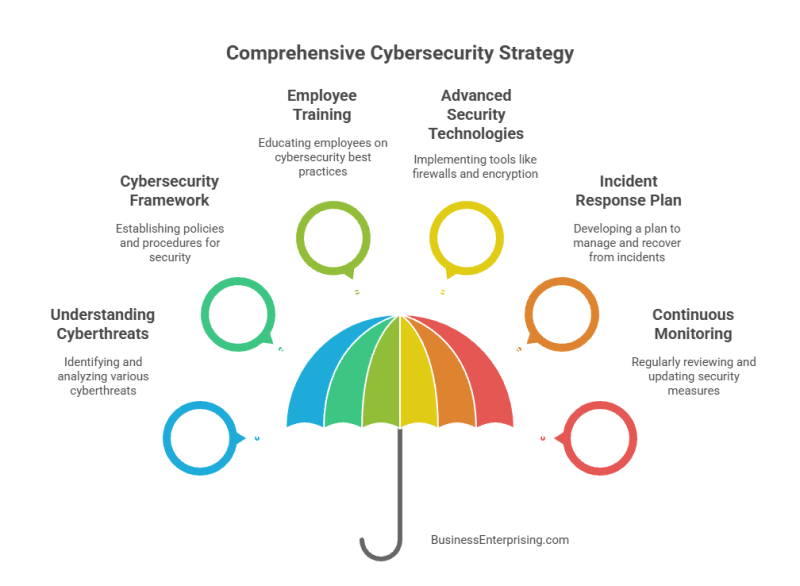
Understanding Cyberthreats
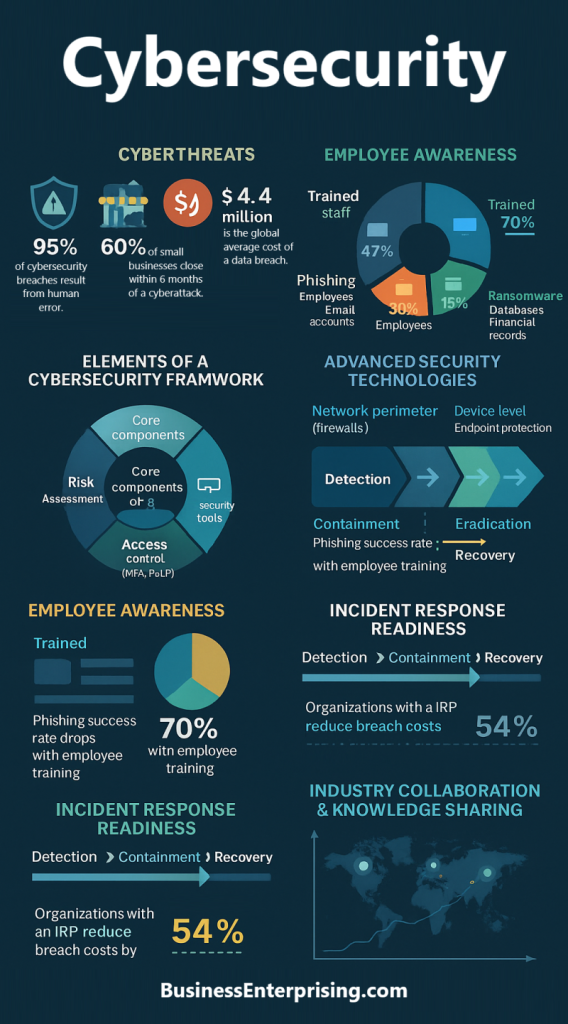
Protection again cyberthreats is critical for businesses with sensitive or proprietary data. Cyberthreats encompass a wide array of malicious activities that target information systems, networks, and data. These threats include malware, phishing attacks, ransomware, and denial-of-service (DoS) attacks, among others. Each type of threat poses unique risks and can exploit different vulnerabilities within an organization’s infrastructure. Understanding these threats is the first step in developing effective defense mechanisms. Malware, for example, is software designed to disrupt, damage, or gain unauthorized access to computer systems. Phishing attacks, on the other hand, use deceptive emails and websites to trick individuals into revealing sensitive information. Ransomware is a particularly malicious form of malware that encrypts a victim’s data and demands payment for its release. DoS attacks flood a network with traffic, rendering it unusable.
The Importance of a Cybersecurity Framework
A comprehensive cybersecurity framework is essential for protecting against cyberthreats. This framework should encompass policies, procedures, and technologies designed to safeguard information systems and data. Developing a cybersecurity framework begins with conducting a thorough risk assessment to identify potential vulnerabilities and threats. Based on this assessment, organizations can implement tailored security measures to mitigate identified risks.
One key element of a robust cybersecurity framework is access control. Implementing strict access controls ensures that only authorized individuals can access sensitive information and systems. This can be achieved through measures such as multi-factor authentication (MFA), which requires users to provide multiple forms of verification before gaining access. Additionally, implementing the principle of least privilege (PoLP) ensures that employees only have access to the information and systems necessary for their roles.
Employee Training and Awareness
Human error is a significant factor in many cybersecurity breaches. Therefore, training employees on cybersecurity best practices is crucial for protecting against cyberthreats. Regular training sessions should cover topics such as recognizing phishing attempts, creating strong passwords, and understanding the importance of data privacy. Employees should be encouraged to report suspicious activities and potential security breaches immediately.
Creating a culture of cybersecurity awareness within the organization can significantly reduce the risk of cyberthreats. This involves fostering an environment where employees understand their role in maintaining security and feel empowered to take proactive measures. For instance, organizations can implement phishing simulation exercises to test employees’ ability to recognize and respond to phishing attempts.
Implementing Advanced Security Technologies
Technology plays a vital role in defending against cyberthreats. Organizations should leverage advanced security technologies to enhance their cybersecurity posture. Firewalls and intrusion detection systems (IDS) are essential tools for monitoring and controlling incoming and outgoing network traffic. Firewalls act as a barrier between trusted and untrusted networks, while IDS detect and respond to potential threats.
Additionally, deploying endpoint protection solutions can safeguard individual devices, such as computers and mobile phones, from malware and other threats. These solutions often include antivirus software, encryption tools, and application control measures. Encryption, in particular, is critical for protecting sensitive data by converting it into unreadable code that can only be deciphered with the appropriate key.
Regularly updating and patching software is another crucial aspect of cybersecurity. Cybercriminals often exploit vulnerabilities in outdated software to gain unauthorized access to systems. Therefore, organizations should establish a patch management process to ensure that all software and systems are up to date with the latest security patches.
Developing an Incident Response Plan
Despite measures for protection against cyberthreats, cybersecurity incidents can still occur. Therefore, organizations must have a well-defined incident response plan (IRP) in place to effectively manage and mitigate the impact of such incidents. An IRP outlines the procedures for detecting, responding to, and recovering from cybersecurity incidents.
The first step in developing an IRP is to establish an incident response team (IRT) comprising individuals with the necessary skills and expertise to handle cybersecurity incidents. This team should include representatives from various departments, such as IT, legal, and communications, to ensure a comprehensive response.
Next, organizations should define the types of incidents that require a response and establish clear criteria for escalating incidents to the IRT. This involves categorizing incidents based on their severity and potential impact on the organization.
During an incident, the IRT should follow a structured approach to containment, eradication, and recovery. Containment involves isolating affected systems to prevent the spread of the threat. Eradication focuses on removing the threat from the environment, while recovery involves restoring systems to their normal operational state.
Continuous Monitoring and Improvement
Cybersecurity is an ongoing process that requires continuous monitoring and improvement. Organizations should regularly review and update their cybersecurity measures to address emerging threats and vulnerabilities. This involves conducting periodic security assessments and audits to evaluate the effectiveness of existing controls and identify areas for improvement.
Additionally, organizations should stay informed about the latest cybersecurity trends and best practices. Participating in industry forums, attending conferences, and subscribing to cybersecurity publications can provide valuable insights into new threats and mitigation strategies.
Collaboration with external partners, such as cybersecurity experts and industry peers, can also enhance an organization’s cybersecurity posture. Sharing information about threats and vulnerabilities can help organizations stay ahead of cybercriminals and develop more effective defense mechanisms.
Conclusion
In conclusion, protection against cyberthreats in the workplace is a critical aspect of maintaining business continuity and safeguarding sensitive information. By understanding the nature of cyberthreats, developing a comprehensive cybersecurity framework, training employees, leveraging advanced security technologies, and implementing a robust incident response plan, organizations can significantly reduce their risk of cyberattacks.
Continuous monitoring and improvement are essential for staying ahead of emerging threats and ensuring the effectiveness of cybersecurity measures. In today’s interconnected world, a proactive approach to cybersecurity is vital for protecting against the ever-evolving landscape of cyberthreats. By prioritizing cybersecurity and fostering a culture of awareness and vigilance, businesses can create a secure environment that supports their operational objectives and protects their most valuable assets.